
Cybersecurity can’t coexist with human error
This article is part of our Opinions section.
Ask yourself: what is the single biggest reason for cyberattacks? Why do cyber defences seem so inadequate, despite the significant investment in cybersecurity?
It’s not due to a lack of effort or spending on cybersecurity measures. And it’s not because of the effectiveness of the tools receiving investment either. In fact, modern cybersecurity technology is quite advanced. So, what is the reason?
The root cause is quite simple. It’s us. Humans are the problem.
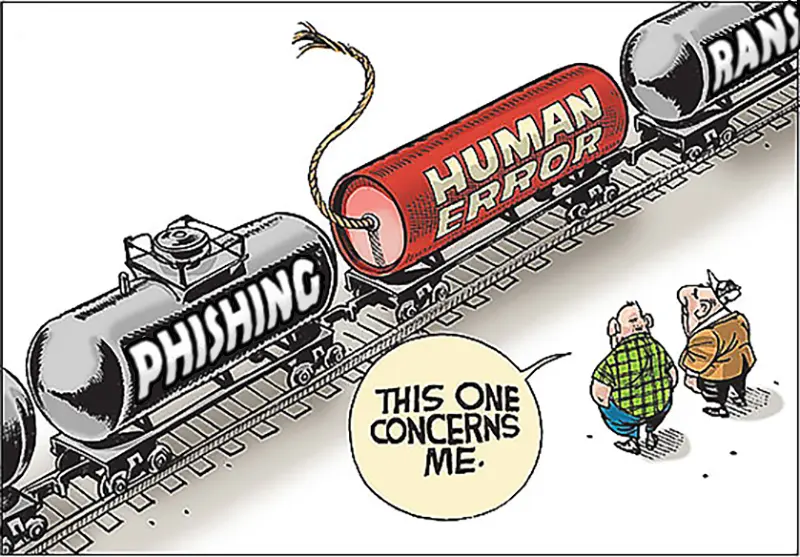
Human error is the root cause of cyberattacks
Human error is the root cause of about 88% of all data breaches according to data from the UK Information Commissioner’s Office.
Cybercriminals know this. They know that attacking identity, the foundation of computer security, is far cheaper and easier. They target credentials such as passwords, browser cookies and private API keys. The data says it all: a Verizon 2023 report proves these credentials show up in 86% of security breaches related to web-based applications and platforms.
This is just one challenge that enterprises face in the cloud-native era. DevOps infrastructure, despite its capabilities, has become increasingly complex over time, meaning that infrastructure heads have lost complete visibility and control over who has access to data. Our identities and the way we manage secure access have become fragmented across various surfaces.
There’s a way out of this tangled access management hellscape: eliminate human error. But this means designing infrastructure to be immune (or at least resilient) to human behaviour.
How can that be done? There are three principles that every company must follow.
Get rid of credentials – all of them
The first step? Ban all ‘secrets’ – every single one. That means removing all static credentials and standing privileges – passwords, cookies, public and private keys, etc.
While these credentials may have worked well within traditional local IT networks that operate on a smaller scale, they are completely incompatible with cloud-native companies operating at a larger scale. As scale grows, the probability of falling victim to vulnerabilities increases exponentially.
It only takes one person opening the wrong file attachment in a phishing email for a bad actor to gain access, not only to their laptop but also to any credentials they can exploit. These credentials can then be used to move laterally across the infrastructure. In fact, 76% of organisations have experienced multiple incidents of account or credential compromise, leading to cybersecurity attacks or lateral movement.
Investing in cybersecurity and observability tools alone won’t prevent catastrophe. You have to base your security on physical world principles, meaning “ephemeral” identity credentials that include biometrics and the hardware identity of the user’s machine. Without this crucial step, you can’t scale a business safely. As soon as you double your workforce, that’s double the risk of human error.
Unify fragmented identities
You might think you have one identity but in today’s cloud-native era? Not so. The concept of identity for developers and engineers is far more complex than it needs to be.
Say your organisation has growing fleets of servers, databases, microservices and DevOps tools speaking incompatible protocols. All of these things track the identities of people in different ways. If your organisation has a multicloud approach, using AWS and Azure at the same time for example, those cloud accounts also track identity in two totally different ways.
And on a more micro level, once inside a cloud account, you might have five Linux servers and five Windows servers. Each of those servers has its own respective internal accounts with its own login credentials. This is how you get an explosion in complexity and proliferation of identity silos.
You can see the problem here: every machine, every cloud and every account essentially becomes an access and identity silo. This has to be consolidated, starting with recognising the important distinction between accounts and identities that are based on real-world physical identities.
Your identity should never be presented as information. Your identity should comprise a combination of your biometric information and hardware identity for the machine you use to interact with the internet. This ‘real-world identity’ should form the basis of what’s used for not just authentication but also authorisation.
Centralise access policy
Every tech company should be able to enforce the rule that ‘developers should never have access to production data’ across all protocols and resource types, for humans and machines, across all data centres and cloud accounts. And yet, for most cybersecurity people today, this concept is total science fiction. What they have instead is a flurry of configurations for users scattered across technologies and geographic regions, without any source of truth for policy across their cloud infrastructure.
Ask any group of infrastructure heads today how long it takes to trace all access relationships attributed to a specific user or resource. You’d probably be shocked by the answer. From experience, the best case you’ll probably hear is a few days if not months. Some don’t have the capability to do this at all. In today’s age of rampant cyberattacks, that’s simply not agile enough.
To address this issue, organisations should explore setting up centralised policy systems that provide this single source of policy truth. That way, organisations can deny unauthorised users from accessing data they shouldn’t have.
Make it inhuman
Every business wants to scale, but scale is the enemy of cybersecurity – the staging ground for human error to occur. If enterprises are to become truly resilient, they have to realise that all the cybersecurity and observability tools in the world won’t fix human error. Such an approach would treat the symptoms of cyberattacks, not the root cause. We need to move the goalpost to well before the point at which a hacker has already breached infrastructure.
Greater adoption of principles of least privileged access, and better visibility of who has access to applications and workloads – these are the things that will bring true resilience to cloud-native companies. By implementing these principles and investing in a holistic cybersecurity strategy, organizations can build a robust defence that protects their data, systems, and reputation from cyber threats.
Now get rid of those passwords!
Related reading: An IT manager’s guide to passwords
More on cybersecurity
NEXT UP
Slow buyers cause tech firms to rethink sales approaches as tough Q1 hits home
New research suggests tech sales were slow in Q1, with buyers of technology and professional services taking their time before committing to any solutions.

ByteDance says it has no plans to sell TikTok and refuses to bow to US pressure
ByteDance, the Chinese company that owns TikTok, stated that it “doesn’t have any plans to sell TikTok” on Toutiao, a social media platform that it also happens to own.

Solace Kidisil, Group COO of Nsano: “The difference between traditional finance and fintech is the questions we ask”
We interview Solace Kidisil, Group COO of Nsano, a fintech company from Ghana, offering digital payment solutions across Africa
