
Zero Trust Network Access for dummies
Brought to you by Palo Alto Networks Zero Trust Network Access For Dummies, Palo Alto Networks Special Edition, consists of five chapters that explore the following: » The changing security landscape, the basics of ZTNA, and the need to move…

Application Management: Racing Ahead of the Competition
Imagine that you’re driving a Formula One car down a track at the Grand Prix. The black-and-white checkered flag is up ahead, signaling that you’re close to the finish line. You need to be fast, but you can’t be reckless…

6 Myths of SIEM
SIEM has changed greatly in recent years, which begs the question, what truly makes a modern SIEM today? This white paper dispels 6 common myths about SIEM. Rumor says SIEM solutions are unwieldy and complex — and therefore only for…

Executive Profiles in Digital Transformation
Insights from C-suite executives who have unlocked their organization’s digital potential Read this eBook to explore how some of today’s top IT leaders – including some names you might recognize – are devising strategies to deliver their organizations real digital transformation…

Guidelines to eliminate the PMO information scavenger hunt
Being responsible for the smooth running of all business projects, the Project Management Office (PMO) is often the linchpin of any successful organization. The department doesn’t just have their fingers in multiple pies, they ensure that all the pies are…

How to Get Your Cloud Costs Under Control
Businesses adopt the cloud to save money and ensure they can innovate and respond to uncertainty. However, while savings generally do come in the long term, some customers see costs rise in the short term. With a strong partner on…

Protección poderosa. Posibilidades poderosas.
La economía digital actual exige que las organizaciones consideren nuevas formas de acelerar la transformación de la TI para obtener mejores resultados del negocio.
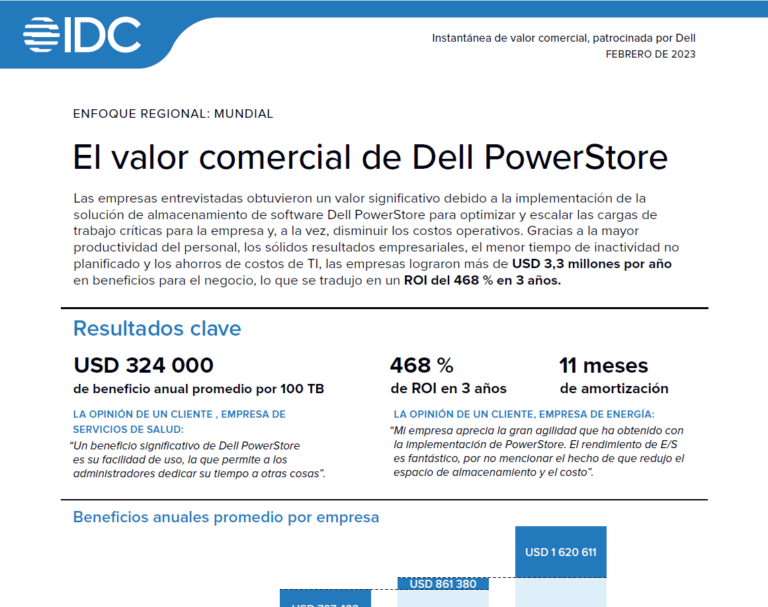
El valor empresarial de Dell PowerStore
Las organizaciones entrevistadas lograron ganancias significativas al implementar la solución de almacenamiento de software Dell PowerStore para optimizar y escalar las cargas de trabajo críticas para el negocio y reducir los costos operativos.

El valor empresarial de las soluciones de infraestructura APEX de Dell Technologies
La investigación de IDC demuestra el valor de utilizar las soluciones APEX de Dell Technologies, las soluciones de protección de datos y almacenamiento hiperconvergente de Dell Technologies.

Creación de resiliencia empresarial para protegerse contra ataques cibernéticos destructivos
Independientemente de la industria, los datos impulsan los negocios en la actualidad. El mercado global depende del flujo constante de datos a través de redes interconectadas, y las iniciativas de transformación digital ponen en riesgo aún más datos.

Protección de datos en un universo multinube
Para cerrar la brecha de protección de datos en sus respectivos entornos de múltiples nubes, la mayoría de las organizaciones confían en soluciones de protección de datos de múltiples proveedores, y esta tendencia va en aumento.

Servicios de almacenamiento de datos de APEX: mejores prácticas de seguridad
Las organizaciones de TI continúan enfrentando desafíos en sus viajes de transformación tecnológica.

¿El almacenamiento de datos está al día con los objetivos de su empresa?
Se espera que la implementación de Storage as a Service crezca mucho.

Optimización del rendimiento con reemplazos frecuentes de servidores para grandes empresas
Los servidores son la piedra angular de la infraestructura de TI moderna. Soportan los requisitos computacionales de toda la cartera de aplicaciones de una gran empresa.

Aproveche la infraestructura tradicional con aplicaciones transformacionales
Es natural que la tecnología sea uno de los principales factores en la apertura de nuevos caminos. Pero si bien cada camino presenta desafíos, también ofrece grandes recompensas.

Aceleradores de servidor. Potencie sus aplicaciones
Para la empresa digital, el éxito depende del aprovechamiento de datos grandes y rápidos.

Deje de administrar. Comience a innovar. Inteligencia diseñada para impulsar su motor de innovación
TI puede dedicar más tiempo y energía a la transformación digital, lo que impulsa la innovación y el éxito empresarial.

Experiencias de TI modernas con costos predecibles
Se gasta demasiado tiempo y dinero en la administración de dispositivos y la resolución remota de problemas.
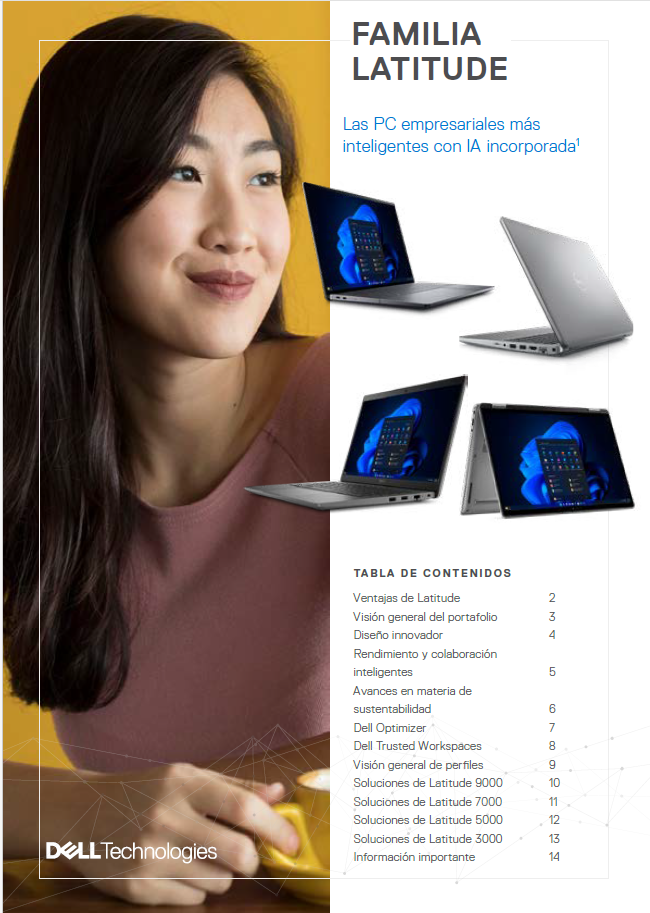
Familia Latitude: Las PC empresariales más inteligentes con IA incorporada
Las PC Latitude presentan características de privacidad, conectividad y colaboración inteligentes para trabajar con confianza desde cualquier lugar, incluido el nuevo panel táctil de colaboración con tecnología háptica en la Latitude 9440 2 en 1.

Diseñar la experiencia de trabajo digital ideal para la próxima generación de innovadores
En este e-Book, se analizan las expectativas de los usuarios para su experiencia de trabajo digital (es decir, las experiencias relacionadas con los dispositivos, las herramientas de colaboración, las aplicaciones y los entornos de trabajo híbrido a los que acceden en el transcurso de su trabajo).