
Octo Tempest: the hacking group that resorts to death threats
Microsoft has warned companies to be on guard from attacks from the Octo Tempest hacking group, which has resorted to death threats among many other malicious tactics.
Microsoft describes Octo Tempest as “one of the most dangerous financial criminal groups”, warning that it uses unusual techniques to target organisations and high-net-worth individuals.
Octo Tempest worms its way into companies in a variety of ways. These range from conventional social engineering, where attackers convince staff to install remote access utilities, through to rarer tactics, such as mobile phone SIM-swapping. Here, they gain control of an employee’s phone number and use that to bypass two-factor authentication.
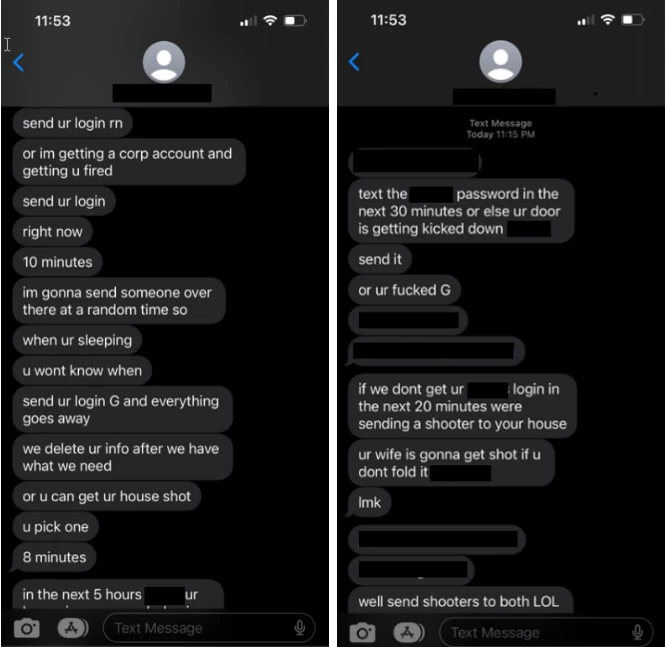
In rare case, Microsoft has also seen the group use stolen personal information such as employees’ home addresses to make death threats. Screenshots released by Microsoft show Octo Tempest attackers threatening to “send a shooter to your house” and warning “ur [sic] wife is gonna get shot” if a target doesn’t hand over logins.
Octo Tempest’s targets: data and cryptocurrency
Once inside an organisation, Octo Tempest is generally after data or cryptocurrency.
“Like in most cyberattacks, data theft largely depends on the data readily available to the threat actor,” Microsoft writes in a lengthy blog on the organisation’s tactics. “Octo Tempest accesses data from code repositories, large document management and storage systems, including SharePoint, SQL databases, cloud storage blobs/buckets and email”.
It goes on to say that Octo Tempest uses “legitimate management clients” such as Azure SQL Query Editor, Cerebrata, DBeaver and MongoDB Compass “for the purpose of connection and collection”.
Microsoft adds that the group “employs a unique technique using the data movement platform Azure Data Factory and automated pipelines to extract data to external actor hosted Secure File Transfer Protocol (SFTP) servers, aiming to blend in with typical big data operations”.
The attackers will normally deploy ransomware after data has been stolen, with recovery made particularly difficult because of the techniques used. “Many of these communications have been leaked publicly, causing significant reputational damage to affected organisations,” Microsoft adds.
Defending against Octo Tempest
Needless to say, defending against such attacks isn’t easy, and Microsoft has a long list of counter measures on its blog. These include constant review and scrutiny of any administration changes, and closely examining the use of any remote admin tools, even those that are already in legitimate use.
Ensuring that only a minimal amount of staff have access to critical workloads is “paramount” to defending against such attacks, Microsoft adds.
NEXT UP
Slow buyers cause tech firms to rethink sales approaches as tough Q1 hits home
New research suggests tech sales were slow in Q1, with buyers of technology and professional services taking their time before committing to any solutions.

ByteDance says it has no plans to sell TikTok and refuses to bow to US pressure
ByteDance, the Chinese company that owns TikTok, stated that it “doesn’t have any plans to sell TikTok” on Toutiao, a social media platform that it also happens to own.

Solace Kidisil, Group COO of Nsano: “The difference between traditional finance and fintech is the questions we ask”
We interview Solace Kidisil, Group COO of Nsano, a fintech company from Ghana, offering digital payment solutions across Africa